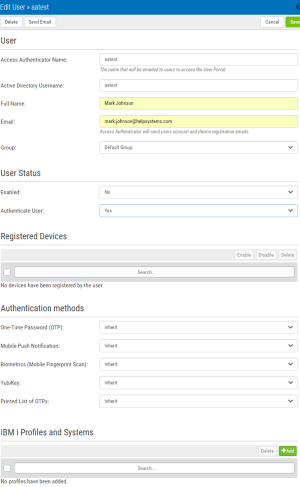
New/Edit User
How to Get There
To add a new User, in the Navigation Pane, choose Users, then click Add > Add User.
To edit an existing user, in the Users screen, double-click a user, or, click  for a User and choose Edit.
for a User and choose Edit.
What it Does
This screen allows Access Authenticator administrators to edit the properties of a user enrolled in the authentication manager. There is some overlap with some of the features provided by the self service portal for the user to edit their own profile. The administrator is able to edit some details that the user can't edit, though (and vice versa). The administrator is able to:
- Add/Edit/Remove IBM i profiles assigned to the user
- Add/Remove devices registered by the user
Options
Delete
Click this button to delete the user in Access Authenticator.
Send Email
Click this button to send the user an email. See Email Settings for details.
Access Authenticator Name
The user profile name. This is the name that will be emailed to users so that they can access the User Portal.
Active Directory User Name
The user name of the User in Active Directory.
Full Name
The full name of the user, used only to identify the user in Access Authenticator.
The email address Access Authenticator will use to send the user account and device registration emails.
Group
The Group the User is assigned to.
User Status
Enabled
Choose Yes to enable the user within Access Authenticator. Choose No to disable the user. Yes must be selected in order for the user to log in.
Authenticate User
If Yes is selected, (and the user is enabled), the user will be challenged to provide the second authentication factor. If No is selected, the user will be able to log in without providing a second authentication factor.
Registered Devices
Devices registered by the user that can be used for authentication are listed here. An administrator can enable, disable, or delete any of the user's devices.
Authentication Methods
For each of the authentication methods, one of the following three settings is possible:
- Disabled. Choose Disabled to turn the authentication method off.
- Enabled. Choose Enabled to turn the authentication method on.
- Inherit. Choose Inherit to use the authentication method defined for the User's Group. If the user's Group setting for an authentication method is set to Inherit, the user will acquire the setting specified in Settings.
IBM i Profiles and Systems
Click Add to begin the process of importing profiles from an IBM i system.
Cancel • Save
Click Cancel to dismiss the screen without making changes. Click Save to create or update the user.