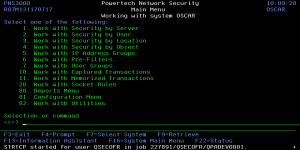
Use the Network Security Main Menu to work with Network Security servers, rules, reports, transactions, configuration, and utilities.
To display the Main Menu, enter the following command on an IBM i command line:
WRKPTNS
Main Menu Options
You can select from the following Main Menu options:
- Work with Security by Server. Select option 1 to open the Work with Security by Server panel where you can you can work with server functions, work with location authorities and work with server user authorities. See Work with Servers for more information.
- Work with Security by User. Select option 2 to open the Work with Security by User panel where you can work with authorities by user.
- Work with Security by Location. Select option 3 to open the Work with Security by Location panel where you can work with authorities by location.
- Work with Security by Object. Select option 4 to open the Work with Security by Object panel where you can work with object security. For more information, see Object Rules.
- Work with IP Address Groups. Select option 5 to work with IP Address Groups. For more information, see Work with IP Address Groups.
- Work with Pre-filters. Select option 6 to open the Pre-filters panel where you can establish a one-to-one relationship between a specific IP address (location) and a user.
- Work with User Groups. Select option 7 to open the Work with User Groups panel where you can maintain User Groups.
- Work with Captured Transactions. Select option 10 to work with captured transactions. For more information, see Working with Captured Transactions.
- Work with Memorized Transactions. Select option 11 to work with memorized transactions. For more information, see Working with Memorized Transactions.
- Work with Socket Rules. The Work with Socket Rules menu offers a launchpad for maintaining Socket Rules. See Work with Socket Rules panel.
- Reports Menu. Select option 80 to work with Network Security reports. For more information, see Reports, later in this User Guide.
- Configuration Menu. Select option 81 to work with Network Security system values, license information, and activation. For more information, see Configuration.
- Work with Utilities. Select option 82 to work with Powertech Secure screen. For more information, see Utilities Menu.
Command Keys
F3 (Exit): Exit the menu.
F4 (Prompt): Provides assistance in entering or selecting a command.
F7 (Select System): Use this command key to work with data from a different System.
F9 (Retrieve): Displays the last command you entered on the command line and any parameters you included. Pressing this key once shows the last command you ran. Pressing this key twice shows the command you ran before that, and so on.
F13 (Information Assistant): Displays the Information Assistant menu with several types of assistance available. Press this key to access more information about the IMB i system.
F16 (System Main Menu): Displays the IBM i Main Menu (MAIN).
F22 (Status): Displays the Operational Resources pop-up window containing the status of several operation aspects of Powertech products.