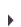Powertech Network Security Architecture
IBM i provides full support to many TCP/IP applications including FTP, TELNET, DDM, ODBC, database serving, print serving, and many others. The following figure illustrates how the unprotected IBM i is available to any networked client tool.

Network Access to TCP/IP Applications without Powertech Network Security
Under this scenario, IBM i object-level authorities are in force. However, there are two main problems with this approach:
- There is no record of who did what! The IBM i server programs do not record who is accessing your system, nor do they record the activity that is performed. For example, a user might use FTP to download the payroll file to their PC, but you have no way of knowing that this has occurred.
- You are relying solely on your IBM i object authorization scheme to control access to sensitive data files and other objects. If your authorization schemes are too liberal, you are allowing access to restricted data. If your authorization schemes are too rigid, you close off access to the data that users need to perform their jobs.
 Previous
Previous