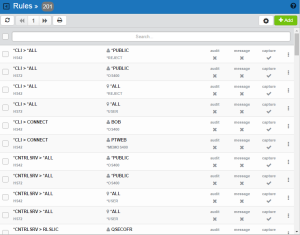
The Rules screen lists all the rules defined by Network Security, including the server and function, user or location, and properties for each. From this screen, you can easily identify specific rules, and edit, add, or delete them.
How to get there
Click the Rules tab on the navigation pane on the left side of the Network Security window.
Options
Selection, sorting, filtering, deleting, and navigation features on this screen are described in Using the Web Browser Interface.
Click a User or Location rule to open the Edit Rule screen, where you can edit the rule.
Add
Choose Add to open the New Rule screen where you can define a new user rule.
Show Actions
Click  next to a rule to show Actions.
next to a rule to show Actions.
- Edit. Choose Edit to open the Edit Rule screen where you can edit the rule.
- Copy. Choose Copy to open the Copy Rule screen, where you can select the system(s) you would like to copy the rule to.
- Delete. Choose Delete to delete the rule.
- Close. Choose Close to dismiss the Action Pane.
Column Descriptions
Server/Function column

This column lists the server ID for each rule. The server ID is the name of the IBM server for which authority is being specified. For a description of servers and functions, see Appendix B: Servers and Functions.
User/Location/Authority column

This column lists the user or location of the rule.
A ![]() icon indicates a User rule. User represents the identity of the person initiating a transaction as a user profile. The special value *PUBLIC, when used on a rule, means that the rule applies to any User lacking a specific rule. When used as a subset or selection parameter, *PUBLIC means to select all such rules for display or printing.
icon indicates a User rule. User represents the identity of the person initiating a transaction as a user profile. The special value *PUBLIC, when used on a rule, means that the rule applies to any User lacking a specific rule. When used as a subset or selection parameter, *PUBLIC means to select all such rules for display or printing.
An ![]() icon indicates a Location Rule. The location is the name of the location for which authority is being specified. The location can be an SNA device, an IP address, an IP Address Group, or the special value '*ALL'. If specifying an IP address, enter either the full IP address or a generic IP address using an asterisk as the final character. IP Address Groups must be established prior to their entry on this screen (see IP Address Groups).
icon indicates a Location Rule. The location is the name of the location for which authority is being specified. The location can be an SNA device, an IP address, an IP Address Group, or the special value '*ALL'. If specifying an IP address, enter either the full IP address or a generic IP address using an asterisk as the final character. IP Address Groups must be established prior to their entry on this screen (see IP Address Groups).
The authority assigned for servers and their functions.
Possible values are:
Aud/Msg/Cap columns

A  or
or  in one of these columns indicates the value is explicitly defined in the rule. A [gray]
in one of these columns indicates the value is explicitly defined in the rule. A [gray]  or
or  indicates the value is not defined in the rule itself, but is inheriting the actual value from another location (much like *SYSVAL in the OS). See Active Rule and Rule derivation.
indicates the value is not defined in the rule itself, but is inheriting the actual value from another location (much like *SYSVAL in the OS). See Active Rule and Rule derivation.
Audit
The audit property controls the type of requests Network Security will log. Possible values are:
 Log all requests by the location/server/function.
Log all requests by the location/server/function. Only log authority failures for the location/server/function.
Only log authority failures for the location/server/function.Message
The message property entry will determine if Network Security sends a message to the Network Security message queue.
 No message is sent.
No message is sent.  A message is sent to the Network Security message queue.
A message is sent to the Network Security message queue. Capture
Capture transactions for Memorized Transaction Request (MTR).
 Do not capture transactions.
Do not capture transactions. Capture transactions.
Capture transactions.